In a world where safety is paramount, the significance of physical security solutions cannot be overstated. These solutions stand as the first line of defense, ensuring the protection of assets, people, and sensitive information. Let’s delve into the realm of physical security solutions and uncover how they create secure environments that empower businesses and institutions.

The Essence of Physical Security Solutions
Physical security solutions encompass a diverse range of measures and technologies designed to safeguard physical assets and mitigate risks. From access control systems to surveillance technologies, these solutions blend seamlessly to create comprehensive security ecosystems.
State-of-the-Art Security Technologies
Access Control Systems
Access Control Systems are security mechanisms that are designed to regulate and control the entry and exit of individuals or vehicles into specific areas or premises. These systems play a crucial role in maintaining the security and privacy of buildings, facilities, and information. They are widely used in various environments, such as residential buildings, offices, data centers, industrial facilities, and more.

Video Surveillance:
Video surveillance, also known as closed-circuit television (CCTV) or security camera systems, involves the use of cameras to monitor and record activities in specific areas. This technology is widely used for security, safety, and monitoring purposes in various settings, such as public spaces, commercial buildings, residential areas, industrial facilities, and transportation systems.

Intrusion Detection Systems:
An Intrusion Detection System (IDS) is a security technology designed to monitor and detect unauthorized or malicious activities within a computer network or a physical environment. IDS plays a crucial role in identifying potential security breaches, suspicious behaviors, and attacks, enabling timely responses to mitigate risks and protect assets. There are two main categories of IDS: Network-based Intrusion Detection Systems (NIDS) and Host-based Intrusion Detection Systems (HIDS).
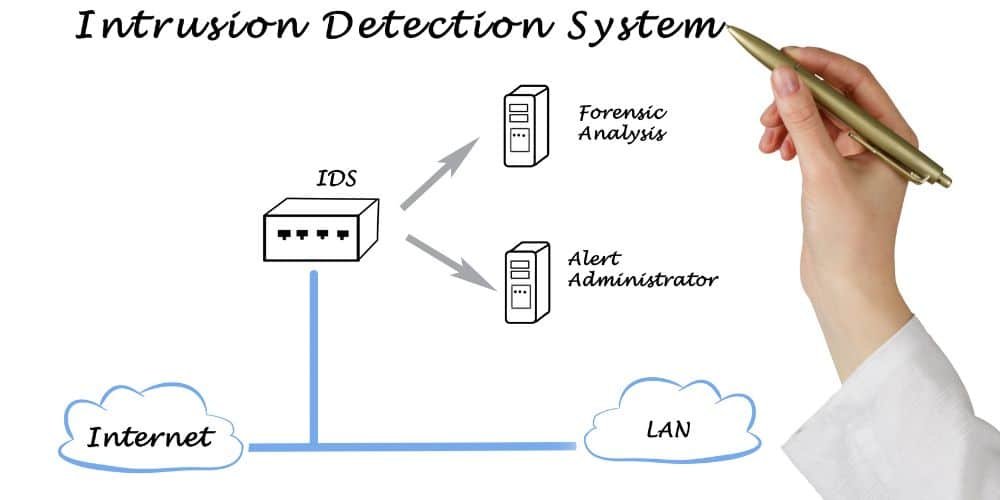
Perimeter Protection:
Perimeter protection, also known as perimeter security, refers to the measures and strategies implemented to safeguard the outer boundaries of a physical space, facility, or property. The goal of perimeter protection is to prevent unauthorized access, deter potential intruders, and provide an initial layer of defense against security threats. Perimeter protection systems can be applied to various types of environments, including residential properties, commercial buildings, industrial sites, and critical infrastructure facilities.

Tailored Strategies for Unique Needs
- Risk Assessment: Physical security solutions begin with a thorough assessment of potential risks and vulnerabilities. This analysis lays the foundation for a customized security strategy.
- Integrated Systems: The strength of physical security lies in integration. Access control, video surveillance, and intrusion detection systems work in harmony to create a robust security infrastructure.
- Emergency Response Planning: In the event of a threat, a well-defined emergency response plan ensures that actions are swift and effective, minimizing potential damage.
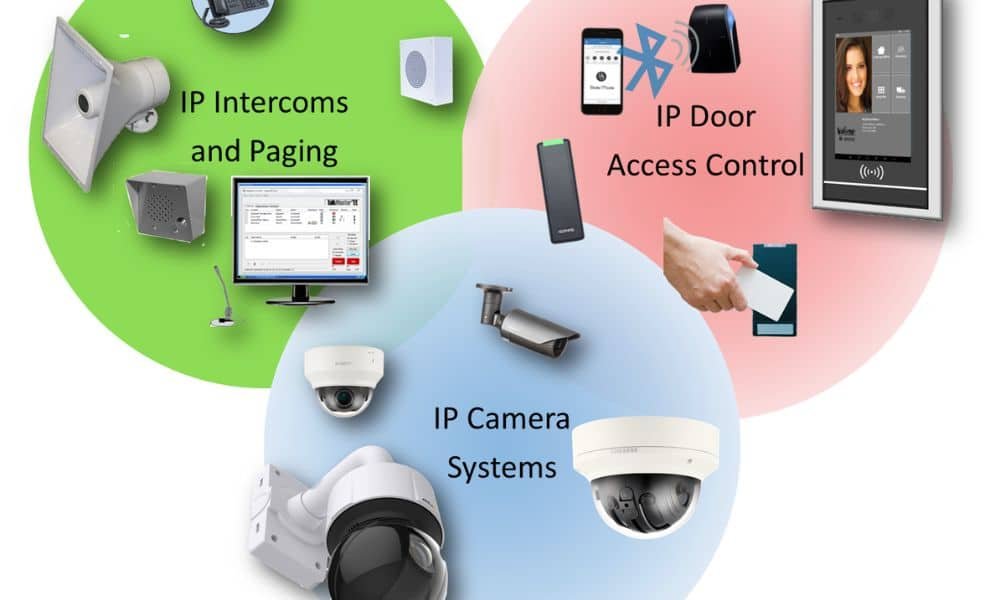
Benefits Beyond Security
- Deterrence: Visible security measures serve as powerful deterrents, dissuading potential threats from targeting the premises.
- Peace of Mind: A secure environment fosters peace of mind among occupants, enabling them to focus on their tasks without worry.
- Regulatory Compliance: Certain industries are bound by regulations that mandate a certain level of physical security. Adhering to these standards is vital for legal and operational reasons.
Choosing the Right Physical Security Partner
Implementing physical security solutions requires expertise, collaboration, and a commitment to excellence:
- Expertise: Choose a partner with a proven track record in designing, implementing, and maintaining physical security solutions.
- Customization: Security needs vary from one organization to another. A reliable partner tailors solutions to the specific requirements of each client.
- Continual Monitoring: Effective physical security is an ongoing endeavor. A trusted partner offers round-the-clock monitoring and support.
In a world where safety is a shared responsibility, physical security solutions stand as stalwart protectors of businesses and institutions. Beyond safeguarding assets, these solutions provide peace of mind, enabling organizations to thrive in secure environments. By partnering with experienced experts, businesses can create an impenetrable shield that not only deters threats but also instills a sense of confidence and trust.

